Network, Computer Security, Computer Network, Network Access Control, Network Security, Security Operations Center, Security Management, Electronics Accessory transparent background PNG clipart | HiClipart

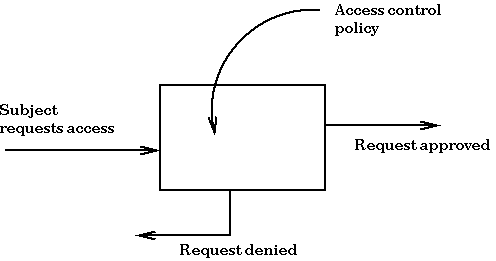
Lecture slides prepared for “Computer Security: Principles and Practice”, 3/e, by William Stallings and Lawrie Brown, Chapter 4 “Access Control”. - ppt download