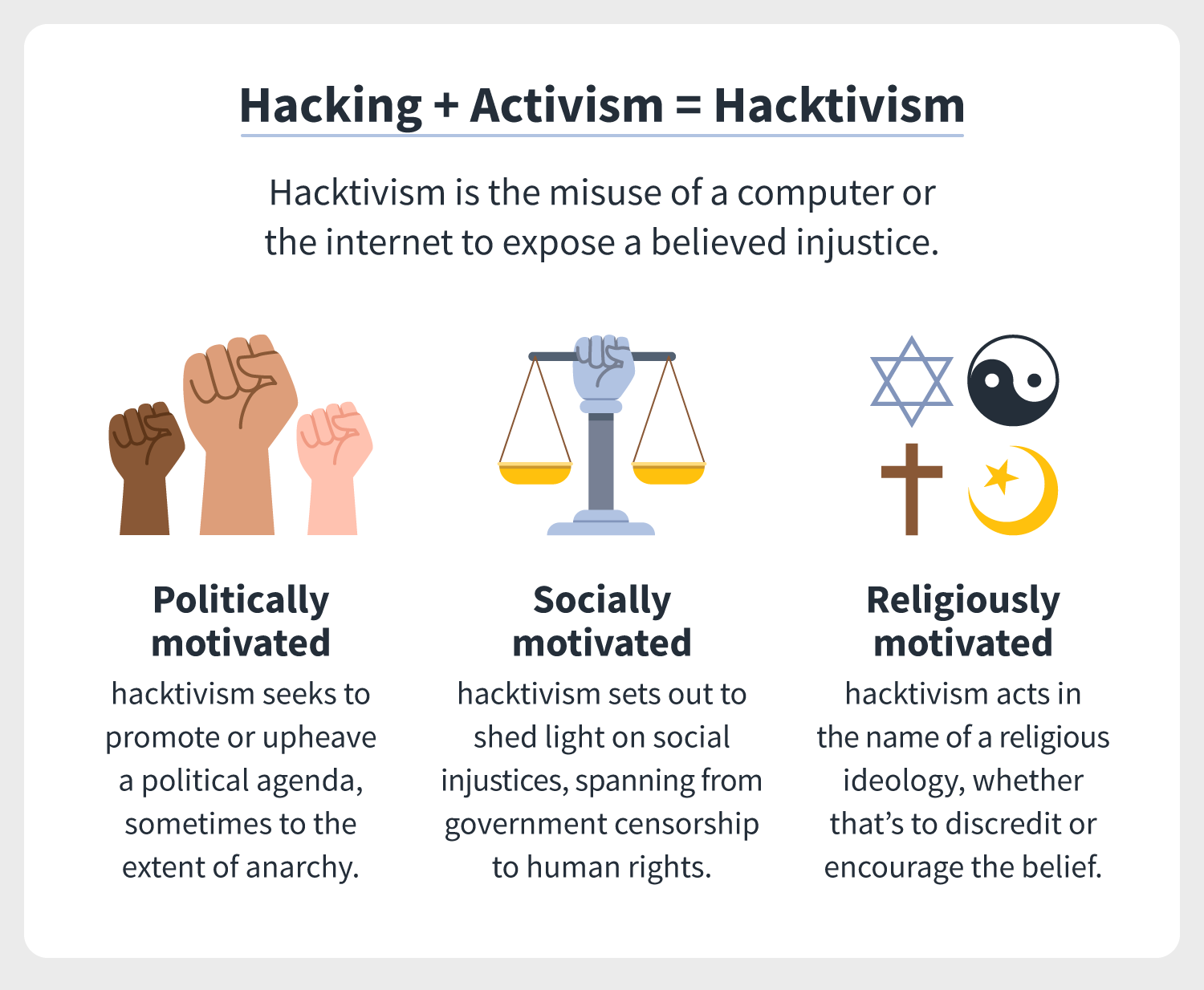
Ebook SOME EXAMPLES RELATED TO ETHICAL COMPUTER NETWORKING HACKING EBOOK de DR. HEDAYA ALASOOLY | Casa del Libro

Hacking With Kali Linux : A Comprehensive, Step-By-Step Beginner's Guide to Learn Ethical Hacking With Practical Examples to Computer Hacking, Wireless ... and Penetration Testing (English Edition) eBook : Bradley, Peter: Amazon.es: